pfSense: Creating a common OOBM network
How-To: Pfsense
Monday 12th May 2025
Background
Asymmetric routing after route filtering was applied
Sometimes it feels like I’m playing an endless game of whack-a-mole; I fix one routing issue but then another pops up. When the LBS prefixes got filtered away from the SAUNA network, I can no longer manage LBS servers, because my computer is in the SAUNA network. The symptom is that I get connected for around 10 seconds and then the terminal freezes. This is likely caused by asymmetric routing:
The connection originates from the SAUNA network and is sent to the firewall (default route).
From the firewall it gets routed to the LBS network.
The LBS router have a route back to the SAUNA network via the VPN tunnel.
This would not be a problem if I move the computer to the LBS network, but then I would have the same problem trying to reach MGMT addresses in the SAUNA network instead.
The best solution for me was to create a common OOBM = Out-of-Bound MGMT network for HTTPS and SSH management. I then prohibit traffic between SAUNA and LBS with firewall rules on the pfSense. To be fair, I knew it had to come to this sooner or later.
Design
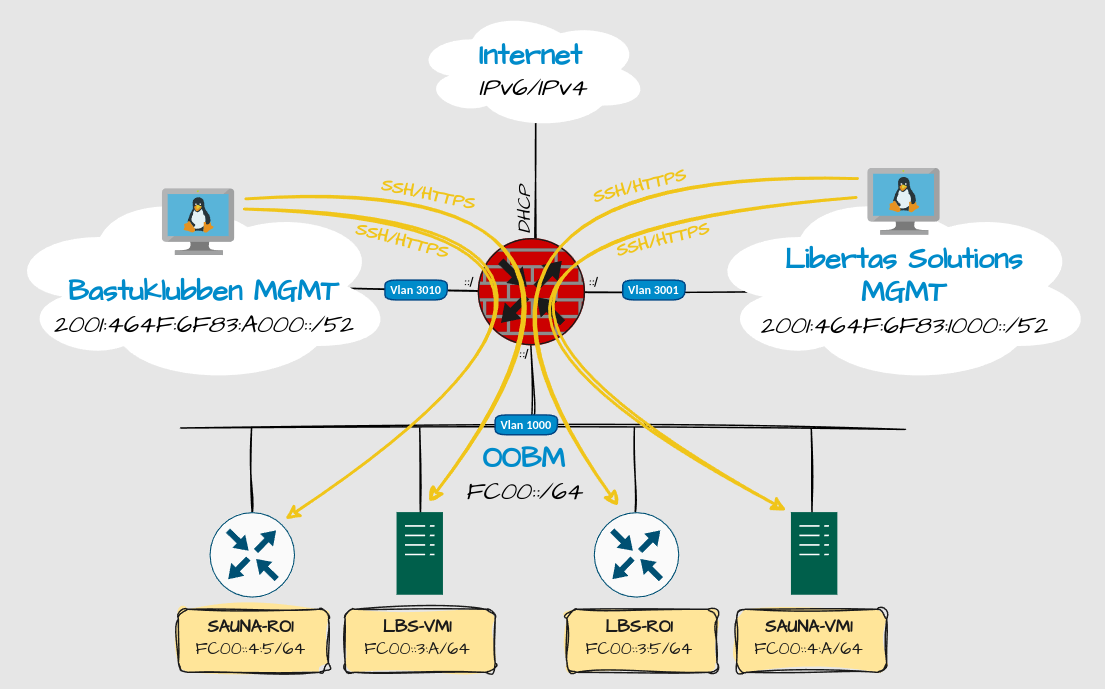
My updated home/work network looks like this:
Explanation:
All servers and network equipment will have a dedicated OOBM MGMT interface in VLAN 1000. From there I can manage both SAUNA and LBS without having to switch VLANs.
Only incoming HTTPS and SSH traffic will use the OOBM interface. All other MGMT traffic will use the ordinary MGMT network routes.
Only incoming HTTPS and SSH traffic is allowed. No outgoing traffic is allowed.
Internet access is not needed so a ULA scope should be fine.
Configuration
pfSense
VLAN creation
I have already written a post on how to create VLAN interfaces on pfSense:
https://opensourceisfun.substack.com/p/pfsense-configure-vlans-on-a-sg-1100
Rules
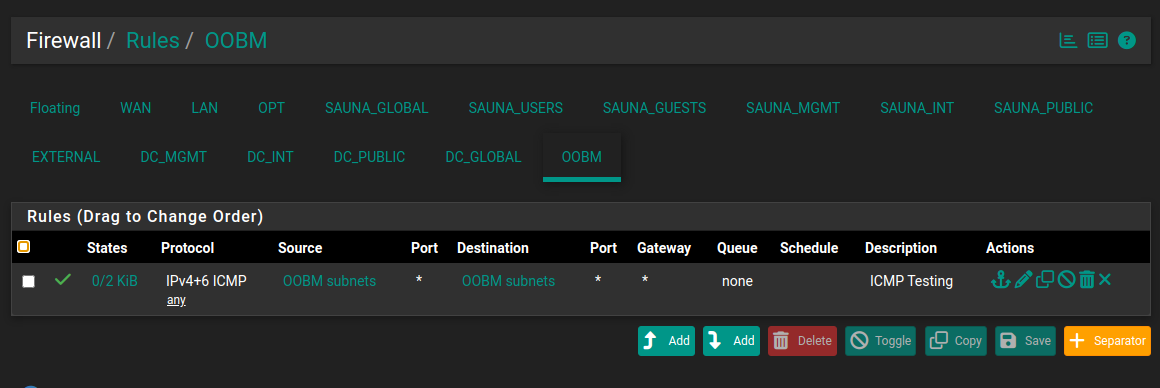
Under Firewall > Rules > OOBM:
Not much going on in here. I’m only allowing incoming ICMP traffic for testing purposes.
pfSense is by default a stateful firewall and only filters packets in the incoming direction. That means that the rules have to be put on the interfaces where the clients are expected to connect from.
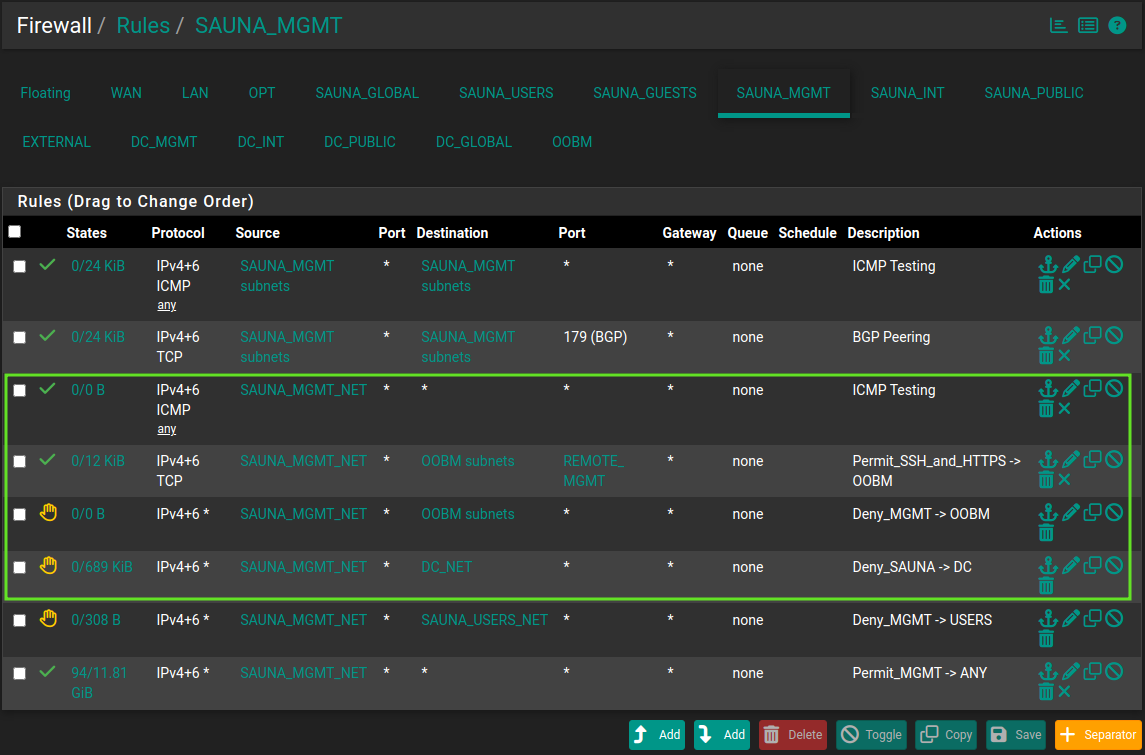
For example, under Firewall > Rules > SAUNA_MGMT, I have created four additional rules:
Explanation:
The first rule permits ICMP traffic to any destination. Not necessary but great for checking reachability.
The second rule matches SSH and HTTPS traffic. I created a port alias to match both 22 and 443 so I don’t have to create more rules than necessary.
The third rule blocks all other traffic to the OOBM subnet. Otherwise it will match the “permit any” rule in the bottom.
The fourth rule rejects incoming traffic towards any LBS network.
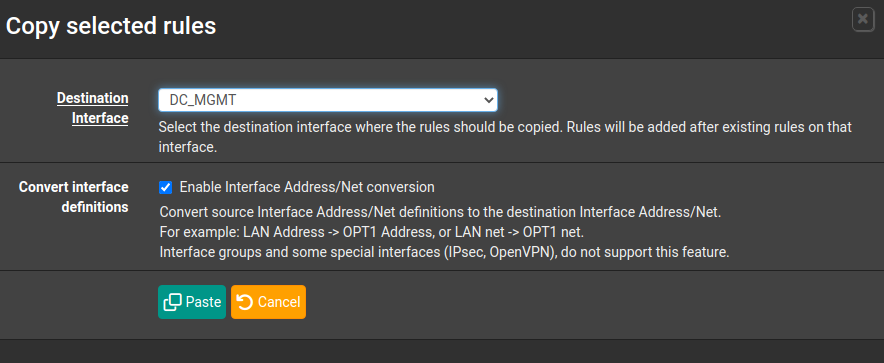
Now i just have to copy those rules to interfaces where they are intended.
Note: Unfortunately, network aliases cannot be converted so they have to be adjusted manually.
Now everything is ready for hosts to connect to the OOBM network. Next post will demonstrate how to configure a Linux Ubuntu 24.04 server to use a specific VRF for SSH traffic.