Proxmox VE Setup Part 5: Firewall
Proxmox VE Setup Part 5

Monday June 9th 2025.
PVE Firewall Concepts
Before configuring the firewall, let’s go through the theory first.
First of all there is some confusion when starting to figure out how everything works. You can find Firewall configuration parameters all over the place:
Datacenter → Firewall
Datacenter → SDN → VNet Firewall
Host-ID → Firewall
Container-ID → Firewall
GuestOS-ID → Firewall
Network device → Firewall
Firewall Rules for Datacenter and Hosts
Datacenter
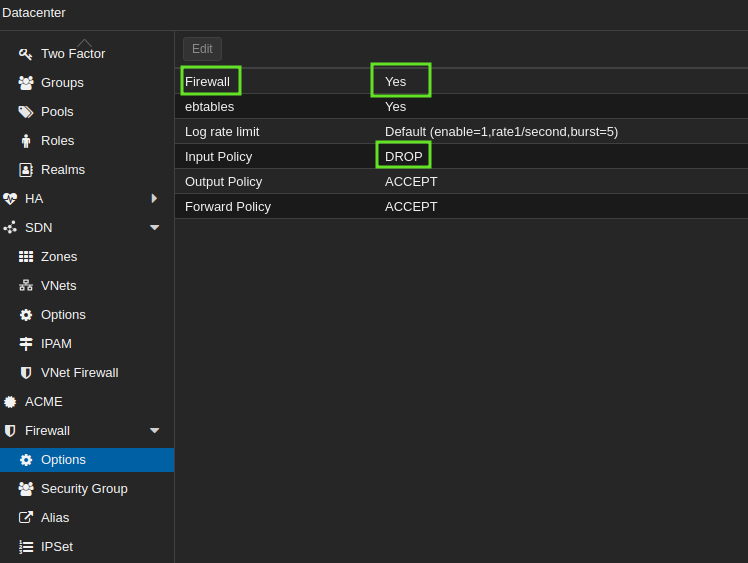
No rules will work, either for PVE Hosts or Guests, if the firewall at the Datacenter level is disabled. Navigate to Datacenter > Firewall > Options to enable it.
Warning: If you activate the DC FW without creating any rules, you will lock yourself out of everything! (already too late I assume?).
If you lock yourself out you have two choices. In the PVE console:
Disable the firewall on the datacenter level by changing the file
/etc/pve/firewall/cluster.fw. (change the BOOLEAN from 1 to 0)disable the firewall on a specific node by typing
pve-firewall stop
Note: Depending on the version of Proxmox, you should still be able to reach the WebGUI if you are connected to the same LAN as Proxmox.
PVE Hosts
Rules created under Datacenter will also be applied to PVE hosts.
Rules created under PVE hosts will have higher precedence than datacenter rules. For example: If SSH is permitted on DC level but denied on the host, SSH will be denied to the host
Default rules
Some rules are implicitly accepted, even if default input policy is set to “drop”. For example:
All local LAN communication is accepted (anti-lockout rule).
IPv6 neighbor discovery is allowed by default.
If you put a "deny any" rule at the host level, you will disable all unspecified traffic, including local LAN traffic.
Firewall rules for Guests and Containers
Rules set on hosts and DC will not apply to Guests and containers.
Local and remote traffic gets implicitly denied when turning on the firewall on Guest and Container level.
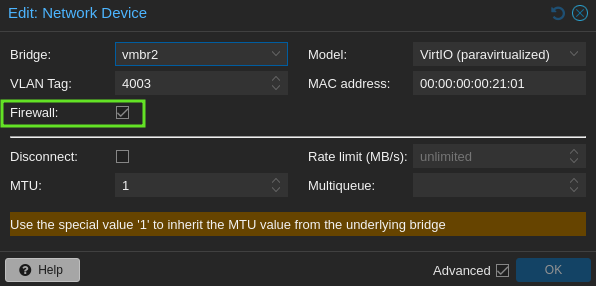
Firewall rules will only be enforced on network cards with the firewall enabled
Important note: The firewall configuration won’t have any effect if no VLAN tag is set on a Linux bridge.
Different Firewall modes
Source: https://pve.proxmox.com/wiki/Firewall#_firewall_rules
iptables-based
The “Classic” Firewall, which I’m currently relying on, is based on iptables. It is identified by the pve-firewall service. It can filter traffic in the incoming and outgoing directions.
root@lbs-pve01:~# systemctl status pve-firewall
● pve-firewall.service - Proxmox VE firewall
Loaded: loaded (/lib/systemd/system/pve-firewall.service; enabled; preset: enabled)
Active: active (running) since Mon 2025-04-07 16:59:06 CEST; 1 month 0 days ago
Main PID: 2309 (pve-firewall)
Tasks: 1 (limit: 38051)
Memory: 101.8M
CPU: 6h 29min 19.828s
CGroup: /system.slice/pve-firewall.service
└─2309 pve-firewallnftables based
A more modern firewall configuration can be found under Datacenter > SDN > VNet Firewall. This is based on the nftables and is identified by the proxmox-firewall service. It filters traffic in the forwarding direction. This means that traffic can be matched when it’s just passing through the host without being terminated to a layer 3 interface. This makes the rule creation more flexible and theoretically should work on Linux bridges without VLAN tagging.
root@lbs-pve01:~# systemctl status proxmox-firewall
● proxmox-firewall.service - Proxmox nftables firewall
Loaded: loaded (/lib/systemd/system/proxmox-firewall.service; enabled; preset: enabled)
Active: active (running) since Mon 2025-04-07 16:59:05 CEST; 1 month 0 days ago
Main PID: 2298 (proxmox-firewal)
Tasks: 1 (limit: 38051)
Memory: 2.2M
CPU: 43min 47.551s
CGroup: /system.slice/proxmox-firewall.service
└─2298 /usr/libexec/proxmox/proxmox-firewallthe VNet firewall is used when you want to create a zone-based firewall. You would basically turn your PVE hosts into advanced routers. Perhaps more on that in a later tutorial. This tutorial will focus more on the classic pve-firewall.
Basic Configuration
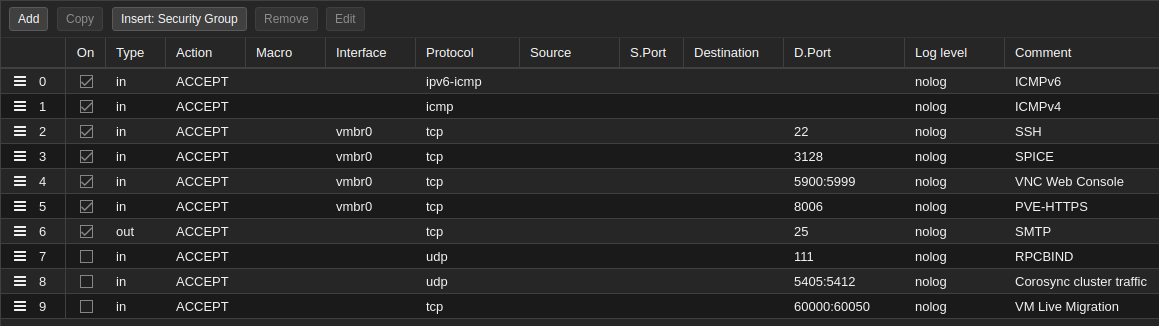
My Datacenter / Host rules
This is my firewall configuration for the Datacenter and is based on the Proxmox Firewall documentation
Explanation:
I have not configured any specific rules for individual hosts, as I am only running one host anyway.
Interface vmbr0 is the management interface. I only allow incoming MGMT traffic on that interface.
PVE uses SMTP to send mail.
Three rules are left disabled on purpose:
RPCBIND is afaik only used for NFT storage. I’m not utilizing that for the moment.
Corosync cluster traffic and VM Live Migration is only relevant if you have more than one node.
Notes about SPICE:
TCP 3128 SPICE Console
From Leo (Brave AI):
SPICE (Simple Protocol for Independent Computing Environments) is an open-source remote computing solution designed for virtual environments, allowing users to view and interact with a computing "desktop" environment, including keyboard, mouse, audio, and video interactions. In Proxmox VE, SPICE provides a way to remotely access virtual machines with enhanced features such as audio and video support, USB device sharing, and folder sharing.
To use SPICE in Proxmox VE, you first need to enable it for the virtual machine. This involves configuring the VM's hardware settings to include SPICE as the graphic card and allocating sufficient video memory, typically 32 MB is sufficient for 4K resolutions. Once configured, you can access the VM's SPICE console through the Proxmox web interface by selecting "Spice" from the "Console" dropdown menu, which will prompt you to download a connection configuration file.
Rule creation
When creating rules:
Warning: the new rules will always be put on top. If you check "enable" at once you may lock yourself out if it's a deny rule
You can specify multiple ports by etiher:
Using comma, i.e. 8006,22
Using colon, i.e. 5405:5412
Not specifying any port or address will permit/drop/reject any port or address
Firewall objects
You can use different kinds of objects to make rule creation simple.
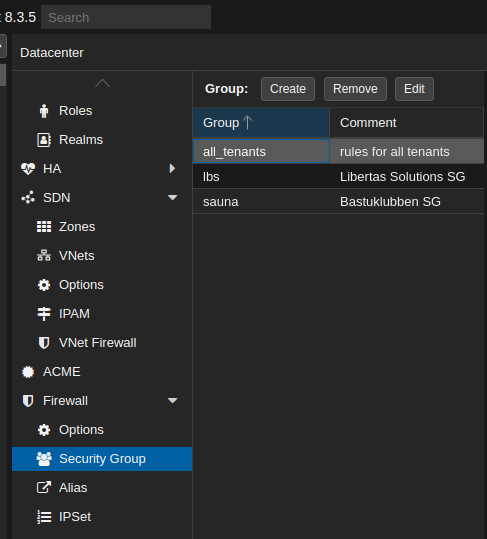
Security Group
Navigate to Datacenter > Firewall > Security Groups
Security groups creates lists of rules that can be applied to multiple guests and containers.
Alias
Navigate to Datacenter > Firewall > Alias
You can define aliases for host IP addresses or networks that is easier to remember than numbers.
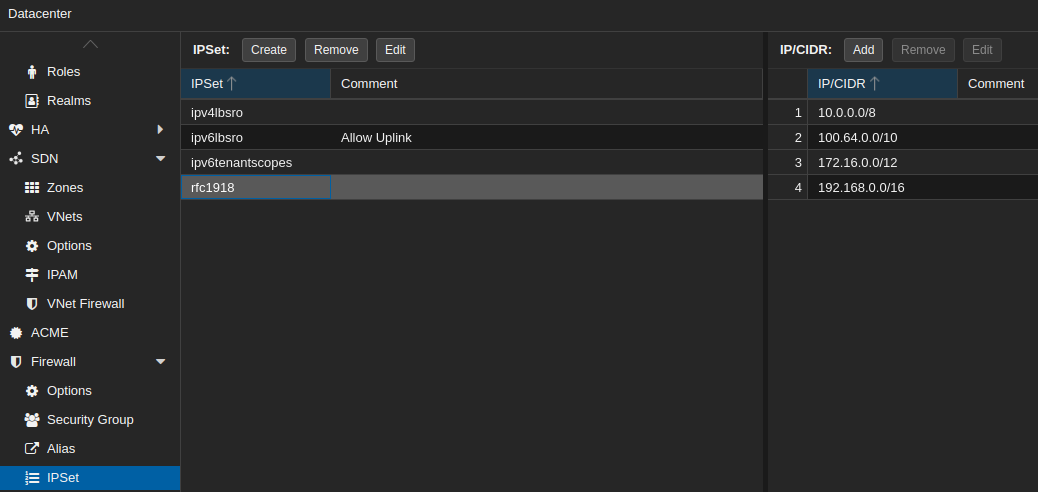
IPSet
Navigate to Datacenter > Firewall > IPSet
Here you can define sets of networks addresses or aliases that can be matched within a single rule.
To be continued…
In the next post I’m going to give a practical example on how to utilize the PVE firewall to prevent guests to communicate between each other.
Special Mention
Thank you David Mckone for the detailed tutorial on PVE Firewall configuration. Unfortunately you didn’t mention that you can’t use Linux bridges without VLAN tagging. However, the Proxmox Firewall Documentation doesn’t mention that either.