pfSense - Open Source Router and Firewall
My first experience with pfSense was around 2012 on a traineeship for an IT business focusing on small to medium sized companies. We were setting up basic networking for a customer but the router hadn't arrived yet. My colleague temporarily used one of his old home PC's and installed pfSense on that as a temporary solution. Since then it's existence has been in the back of my head hibernating, until now.
pfSense is kept in development by Netgate and is based on the FreeBSD Unix-like distribution. The software is free to use, but Netgate also have a line of appliances. I bought a SG-1100 after some stability issues with BGP. It seems that some servers are just not built for advanced networking. So far I'm very satisfied with it.
Functionality
FreeBSD is designed for advanced networking operations, therefore pfSense have tons of features. You can even download external packages for even more features with the packet manager. For example, I just found out that you can install Bind DNS server. The Firewall is the center of the network, so it makes perfect sense to have a DNS service there, at least for a small to medium sized network.
The only thing that doesn't seem to be supported is multiple FIB = Forwarding Information Bases (VRF in Cisco speak). FreeBSD have the capability to handle that, but there is just no way to configure it from the GUI. There is however a way to do it, using tunables. Tunables makes it possible to implement shell commands from the GUI. It is however, quite advanced stuff. I have had to use tunables for TrueNAS, another open-source software based on FreeBSD. I'm going to explain that in a later post.
Where does it fit in
I'm not a firewall expert, but looking at all the available capabilities, I believe pfSense could fit in anywhere; from the home up to large corporations. The only thing might be the limited support because of its niche. The main reason people choose Cisco or Microsoft is absolutely not because of the cheap cost, but for the knowledgebase. Therefore, I do not expect to see this in any large corporations, even though it might be able do the job. (Perhaps Netgate can prove me wrong on that one day).
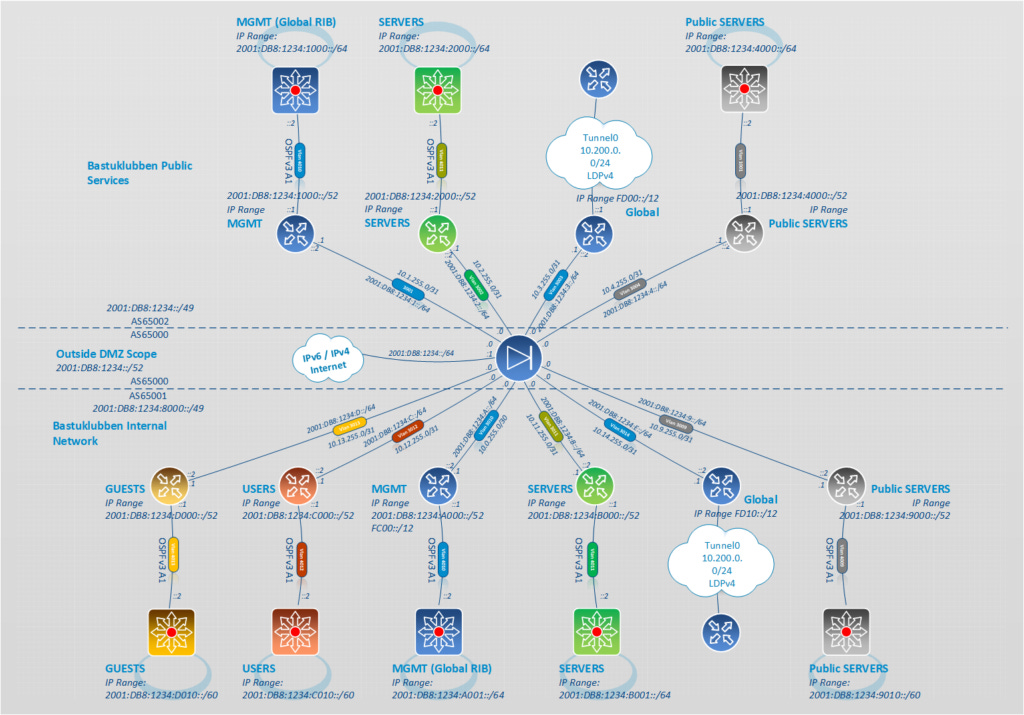
I consider myself to be a quite advanced user. Personally, I'm using the pfSense for inter-VRF routing and Internet Connectivity. Here is my design, the pfSense is in the middle:
Note: The above networks in AS65002 are not finished yet. I still need to aquire some additional hardware.
I have already made a blogpost on how to setup BGP between a Cisco Router and a pfSense firewall:
Configuring BGP Peering between pfSense and Cisco.
Experience so far
I must say that compared to many other software I have tested the last 2 years, pfSense have been a quite pleasant experience. Their documentation is superb, and many things you configure, actually work in the way you think. The only major problem I had was the stability issues with BGP, as I mentioned earlier. That was solved with the SG-1100 appliance.
Another minor problem I ran into is that you can't define your own IPv6 Link-local addresses to the interfaces. This is not a pfSense bug, but a FreeBSD bug. Apparently it hasn't been a priority to fix it. However, there is a workaround by including the scope id inside the link-local address.
Recommendations
These are my recommendations, based on my knowledge with networking and experience with the pfSense software. In no way any advice:
For more advanced networking than just regular home usage, buy an appliance. It's worth the investment to have a stable network. It's totally OK if you want to try out the software on a virtual machine first. Just be aware that you might get frustrated.
If you run it on a VM, consider the server location and what happens when the server goes into maintenance mode. This is also a reason why I think a physical firewall is more preferred, but it depends on the environment.
This is speculation but I would assume, in a all virtualized environment with supported hardware, it makes sence to run it on a VM.
If it is a mix of virtual and physical appliances or users in the network, a physical firewall is preferred.
Make sure the WAN interface have direct Internet connectivity. It's really difficult to import a backup file with features from the packet manager if you don't.
In a setup like mine, 3 ports should be used at minimum:
The LAN port is used as a OOBM interface where I access the GUI. How to setup a OOBM interface will be a future blogpost.
The WAN port is used to connect uplink to the ISP.
The OPT1 port is used for inter-VRF routing by setting up subinterfaces. Setting up subinterfaces on the SG-1100 was a bit tricky, so I'm going to cover that in a future blogpost aswell.
pfSense only processes rules on ingress of a port. Something to consider when you are setting up firewall rules.