Nextcloud Talk: Setting up a HPB = High Performance Backend
How-To: Nextcloud Talk
18 December 2023
Updated 28th January 2024
Updated again 29th January 2024
Nextcloud Talk Traffic patterns
Nextcloud Talk is a video conferencing tool that can be used within Nextcloud. Depending on what desired usage, you may need a STUN server and and a TURN server. Reading from Nextclouds documentation, in short:
Clients first tries to establish P2P = peer-to-peer connections between each other. This works fine inside a local network without any additional utilities.
When there is need for NAT traversal, which in most cases it is, you may need to setup a TURN server. Talk traffic will then not be P2P, but relayed through the TURN server.
Nextcloud Talk will try direct P2P in the first place, use STUN if needed and TURN as a last resort fallback. Thus to be most flexible and guarantee functionality of your Nextcloud Talk instance in all possible connection cases, you most probably want to setup a TURN server.
Installation of the Nextcloud HPB
The Nextcloud HPB includes all the required components for Nextcloud Talk to work properly (except recording backend). To be honest, I’m not sure if a HPB is actually needed (NAT is a very confusing subject), but at least it will offload the Nextcloud server and make the solution bullet proof for all possible connections.
There has been some serious community work to get the installation of STUN and TURN to be as streamlined as possible; there is no need to set up any components from scratch anymore. There are 2 recommended ways one could install a high-performance backend:
Install the nextcloud all-in-one server. Then all services are pre-configured and you don’t need to do anything.
Install the standalone HPB and connect it to your Nextcloud server. The benefit of this is that you can have the HPB and the Nextcloud server on separate hardware.
In this article I’m going to explain how to install the standalone HPB and make sure it works properly.
Note: for recording to work, you need to install an additional recording server.
Install the Nextcloud Standalone HPB
Requirements:
A VM with Debian 11 or 12 to install the software on (recommended by the developers)
Mailserver (nice to have, but not required)
Nextcloud Talk (duh)
Note: The instructions says it requires a public IPv4 address, but that is not true.
Ports that need to be opened in the Firewall:
TCP and UDP 5349 (STUN Server with TLS)
Alternatively TCP and UDP 3478 (STUN without TLS)
TCP 443 (HTTPS for the initial establishment).
Note: If you only have one IPv4 address, you will need to setup the Standalone HPB to work behind a Reverse Proxy, together with the Nextcloud Server. However, if the clients are running dual-stack, it will still work without RP.
Install instructions
Note: Following instructions assumes no Reverse Proxy, but configuring it to work behind a RP is not a big deal. You just need to change the NGINX settings to point to your internal CA, instead of using certbot.
Perform following tasks as root:
sudo su
apt install openssh-server unzip wget sudo
cd /root
wget https://github.com/sunweaver/nextcloud-high-performance-backend-setup/archive/refs/tags/1.2.6.zip
unzip 1.2.6.zip
cd nextcloud-high-performance-backend-setup-1.2.6
./setup-nextcloud-hpb.shThen follow the instructions on this link:
https://github.com/sunweaver/nextcloud-high-performance-backend-setup/wiki/02-Setup-Script
The Github link explains well enough how to install the server. It’s an automatic script where you just enter some domain information.
Note: The installation script includes options for Collabora Office too. That part is out of scope for this guide.
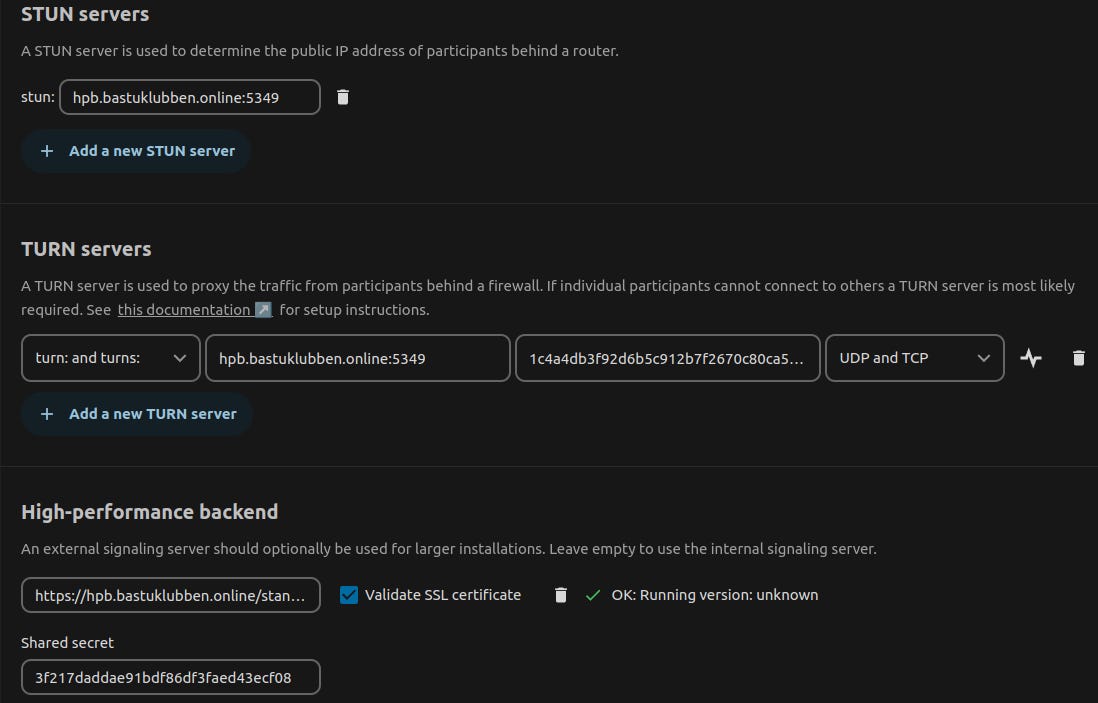
Result
STUN server = hpb.bastuklubben.online:5349
TURN server:
- 'turn and turns'
- turnserver+port: hpb.bastuklubben.online:5349
- secret: 1c4a4db3f92d8b5c912bNOTREALSECRET6a3ed04416d7ba606f1a0222d506
- 'udp & tcp'
High-performance backend:
- https://hpb.bastuklubben.online/standalone-signaling
- nextcloud.bastuklubben.online -> 3f217daNOTREALSECRET3faed43ecf08
======================================================================
SSL certificate we're installed successfully and get refreshed
automatically by Certbot.
Notifications regarding SSL-Certificates get sent to:
- 'wl@bastuklubben.online'
======================================================================
Nginx got installed which acts as a reverse proxy for your selected
services.No extra configuration needed.
======================================================================
The msmtp package got successfully configured. So this system can
send emails to you now. You should have got a test email. Please
have a look and make sure you also look into your spam folder.
=== MSMTP Setup ===
E-Mails get sent to: wl@bastuklubben.online
E-Mail account username: wl@bastuklubben.online
E-Mail account password: *****
E-Mail server host: mail.bastuklubben.online
E-Mail server port: 587
======================================================================
Thank you for using this script.Notes:
Certbot supports IPv6, so you do not need an IPv4 address for this purpose
The install script will ask for a mailserver. If you don’t have one yet, just enter a bogus name.
Minor edits
The script assumes direct IP connectivity. coTURN settings needs to be modified for NAT (if applicable). Look for these lines in the following file:
nano /etc/turnserver.conf
listening-ip=10.9.1.67
relay-ip=10.9.1.67
external-ip=${PUBLIC_IP}/10.9.1.67Note: I have written a cron task to perform a public IP lookup hourly:
root@sauna-hpb:~# nano /etc/cron.d/publicIP
# crontask to update the PUBLIC_IP environment variable every hour by using a IP-Checker tool.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
0 * * * * root PUBLIC_IP=$(curl -s https://dyndns.loopia.se/checkip | grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b")Change the SSL Certificate (Optional)
If you don’t want to use Let’s Encrypt certificate, you can edit the NGINX settings to look for a different certificate:
nano /etc/nginx/sites-enabled/nextcloud-hpb.conf
...
ssl_certificate /etc/ssl/certs/SAUNA-HPB.pem;
ssl_certificate_key /etc/ssl/private/SAUNA-HPB.key;
ssl_trusted_certificate /etc/ipa/ca.crt;
...systemctl restart nginx
UPDATE: Apparently you also need to update the TURN server configuration with the correct certificate. Otherwise the call establishment won’t work from outside networks.
nano /etc/turnserver.conf
...
# Certificate file.
# Use an absolute path or path relative to the
# configuration file.
# Use PEM file format.
#
cert=/etc/ssl/certs/SAUNA-HPB.pem
# Private key file.
# Use an absolute path or path relative to the
# configuration file.
# Use PEM file format.
#
pkey=/etc/ssl/private/SAUNA-HPB.key
...systemctl restart coturn
systemctl restart janus
Nextcloud Configuration
As the admin user, go to Adminstration Settings > Talk
Enter following settings:
Explanations:
The turn server secret corresponds with the static-auth-secret inside /etc/turn.conf on the HPB.
The HPB Shared secret corresponds with the [nextcloud-backend-0] secret value of the file /etc/nextcloud-spreed-signaling/server.conf
Special Mention
I want to thank everyone at the Nextcloud Community whom have made the installation of such a complex server, to be so (relatively) simple to setup.
Appendix
Knows Caveats
Nextcloud Talk connection problems with Firefox browser.
As of 29th January 2024, I thought I had everything fixed and properly tested yesterday when I adjusted the certificate settings inside the turnserver.conf file. But my friend still had connection issues when joining the call. Even though if I was able to join from multiple computers on different 4G networks, to test connecting from an outside network.
It turned out that it was the Firefox browser! When switching to a chrome-based browser (Brave), it worked like a charm.




Thanks for this detailed tutorial, I'll use it this week-end 😃
You mentioned you were moving to Nextcloud AIO, may I know why? Since you've done the hard part of installing and connecting a HPB server, what's the advantage of reinstalling everything (Nextcloud, Collaboration, HPB...) on a single server, maintainability?
I'm considering using Hetzner storage share deal to host Nextcloud (large affordable HDD storage) and use external dedicated VPS to get Collaboration + HPB functionalities. Do you think it's better to go with AIO (and eventually connect external storage to increase disk space)?
The page you linked to to "follow the script" is written in German. Tough to follow.