Network Fundamentals Part 3
The Transport Layer
Layer 4: The Transport Layer
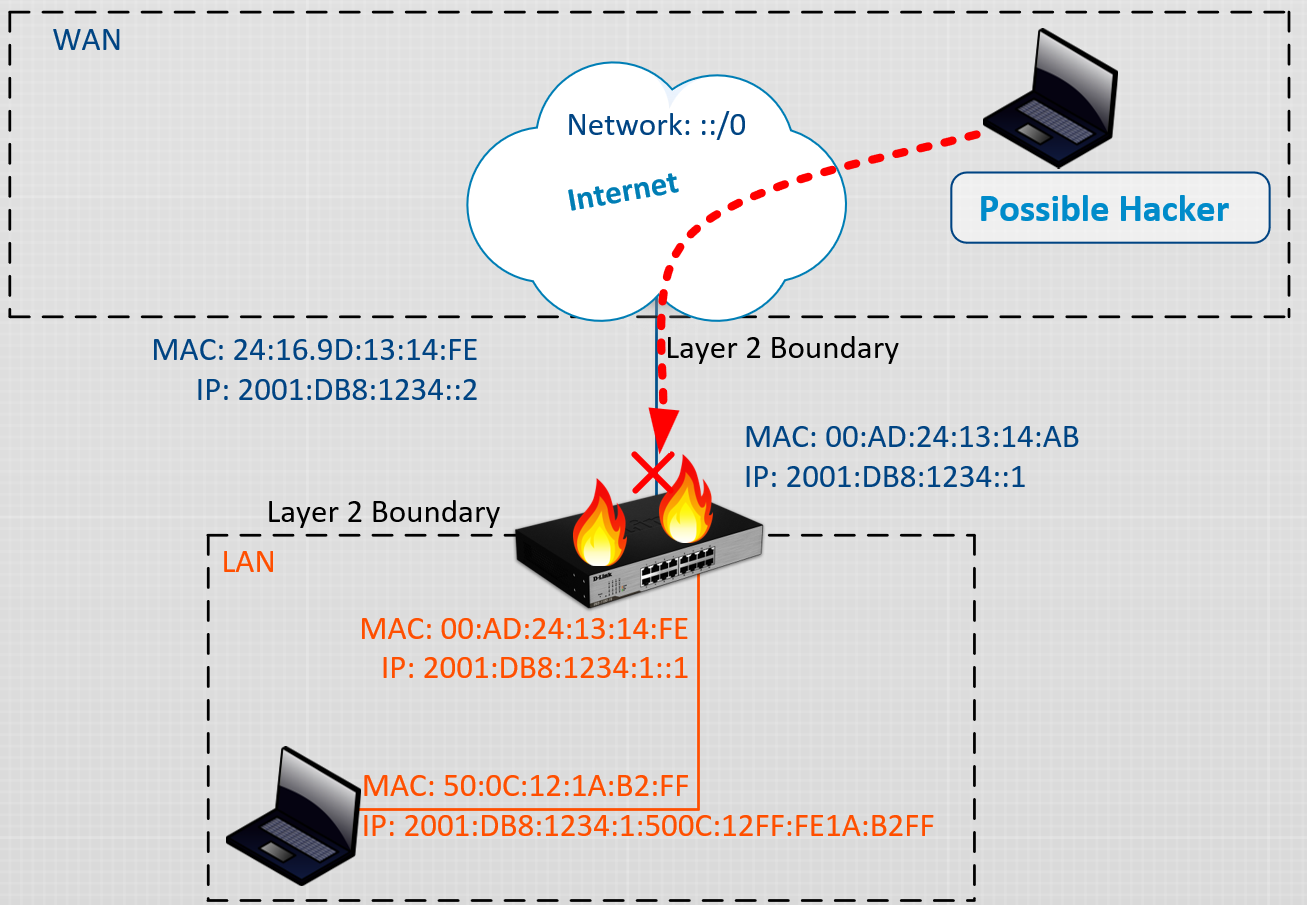
Up until this point I haven’t mentioned much about security. The Transport Layer could also be nicknamed the Firewall Layer. It focuses on basic access rules between the Internet (the WAN = Wide Area Network) and your home network (the LAN = Local Area Network).
With only switching and routing in place, all traffic are permitted to enter your home network and your devices. That is of course a huge security risk. There are hardly any need for a private home devices to be publicly reachable on the Internet. For this reason, a firewall is needed.
Most home routers have basic firewall functionality. While it is possible to block certain Layer 2- or Layer 3 addresses from communicating with each other, that is not enough. You still want to be able to initiate a connection with the outside, but you don’t want the outside to be able to initiate a connection to your devices. The most basic home routers always have that rule; it permits all outgoing traffic towards any destination, and blocks all incoming traffic, unless it was initiated from the inside. The firewall keeps a session table to keep track of all connections as long as they are active. For example: while someone is browsing a website, all traffic between the client and the webserver is permitted.
Checkpoints definition of a firewall:
https://www.checkpoint.com/cyber-hub/network-security/what-is-firewall/
Note: Client Computers may also have a firewall installed, for last line of defense.
How does a firewall filter specific traffic?
There might be times when you actually need to allow incoming traffic for a specific service in your home. For example, you have a son (or yourself) with a Minecraft server that needs to be reachable from the Internet, so that your, or your sons friends, can connect to it. At the same time you don’t want to permit all traffic to that computer, you just want to allow Minecraft communication. That is when Layer 4 protocols are being introduced.
Before we discuss the different Layer 4 protocols, let’s build on the previous analogies from Part 1 and Part 2:
First Scenario: Someone sends a packet to you (they somehow found out your home address). However, there is a security guard at the front door (Mr Firewall Guy), and he doesn’t recognize the sender, so he discards the packet before it arrives to you.
Second Scenario: You send a letter to a to a business that makes… beer googles. The letter passes through the security guard at the front door and he makes a note that if something from that specific company arrives related to beer googles, then that postman should be let in.
Third Scenario: Maybe you are the beer googles producer and you want to allow any letters regarding customer service or order requests to your co-worker in a specific area right behind the main door.
Different Layer 4 protocols
The most common Layer 4 protocols are TCP and UDP.
TCP = Transmission Control Protocol
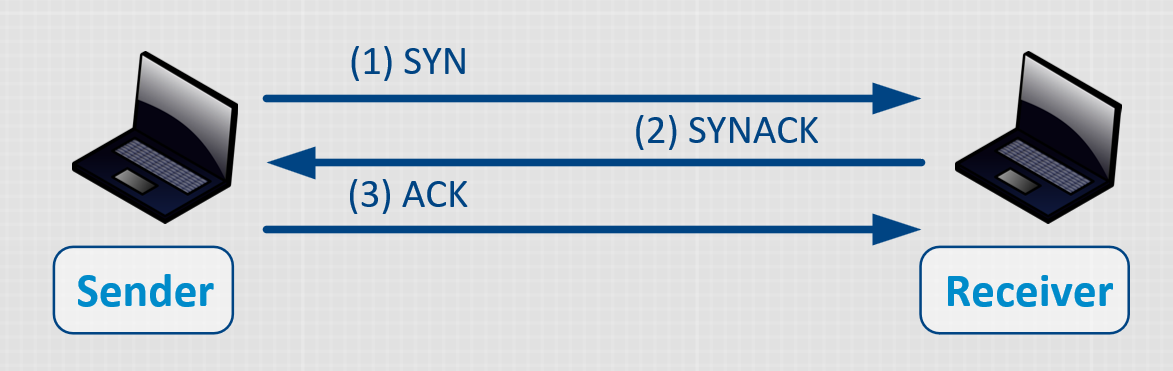
This is when the TCP from the TCP/IP model is introduced. TCP is a connection-oriented protocol. It establish a connection between 2 computers with a 3-way handshake:
Sender (SYN): “Hi, I want to start a communication with you. Can you acknowledge?”
Receiver (SYNACK): “Acknowledged. Let’s start a communication. Can you acknowledge?”
Sender (ACK): “Acknowledged” *communication starts*
Every packet sent after the 3-way handshake is then acknowledged by the other end. If a packet is not acknowledged, a retransmit of that packet occurs.
TCP is used for applications when reliability is the biggest concern. For example, when you are browsing webpages, that application is built on TCP.
UDP = User Datagram Protocol
UDP is a connectionless protocol. It means that traffic is just sent and then hope for the best that the traffic is received on the other end.
I’m about to tell you a UDP joke, but I’m not sure you will get it
UDP is primarily used for real-time applications; like voice and video streaming.
TCP and UDP Port Numbers
So how does the firewall utilize TCP and UDP to permit or deny specific applications? Every application have a dedicated TCP or UDP port number. The total range of TCP and UDP port numbers available are from 0 - 65535.
The Well-Known Port Numbers
0 - 1023 are the reserved well-known port numbers assigned by IANA. These ports are reserved for network-related protocols and should never be used for custom applications.
Examples of well-known TCP Port numbers:
53: DNS = Domain Name System. (Both UDP and TCP). A common service on the Internet to translate webpages like “example.com” to an IP address.
80: HTTP = Hypertext Transfer Protocol (unsecure). Used to browse websites but is mainly replaced by HTTPS.
220: IMAPv3 = Internet Message Access Protocol Version 3. Used for e-mail services.
443: HTTPS = Hypertext Transfer Protocol Secure. The most used method of browsing webpages today. HTTPS is more safer than HTTP because it involves digital certificates to check the authenticity of the webpage and also encrypts the communication.
Examples of well-known UDP Port Numbers:
53: DNS = Domain Name System. (Both TCP and UDP)
67: DHCP Server Messages. Dynamic Host Control Protocol is used to assign IP addresses to client machines without having to manually configure them.
68: DHCP Client Messages.
The Registered Port Numbers
The port numbers between 1024 and 49151 are the registered port number range. You can apply to IANA to get a specific port number for your application. The same port registered to you however, may be unofficially used by other applications.
Note: a list of well-known and registered ports exist here:
https://tcp-udp-ports.com/ports0-1000.htm
Dynamic Port Numbers
The port numbers between 49152–65535 are designated for private or dynamic ports. Example usage of dynamic ports:
HTTP Clients uses a dynamic TCP ports when connection to a website.
RTP = Real-time Transmission Protocol can be used when streaming audio and video. It utilizes custom UDP ports for sending audio and video packets.
To sum it all up: A firewall can allow certain TCP or UDP port numbers into the network. In the IT world we refer to this as “punching holes” in the firewall to let certain traffic through.
Privacy concerns regarding TCP/UDP
The well-known ports only tells what type of application that a client is communicating with. For example, TCP port 443 indicates that the user has a connection with an application that is using HTTPS for communication. It could be connecting to a website, making a RESTful API call, or perform any web-based application utilizing HTTPS for transferring data. No more specific information than that can be recognized by TCP and UDP Well-Known Ports.
When an application is using a custom port in the registered range, it is not possible to determine with absolute certainty what type of application it is, because many applications are using the same registered ports unofficially. However, many applications are using default ports and can be assumed. For example, If your ISP is seeing TCP and UDP traffic on port 2456, it could indicate that you are playing the computer game Valheim. Wikipedia have a list of official and unofficial registered ports.
There exists more advanced firewalls that are capable of performing something called deep packet inspection, but that is for the next article.
ICMP = Internet Control Message Protocol
TCP and UDP are ~90% of all the Layer 4 traffic on the Internet, but there are more. One in particular that is worth mentioning is the ICMP = Internet Control Message Protocol.
For IPv4, this protocol is mostly used for reachability testing. For IPv6, it is a fundamental building block.
ICMP doesn’t have port numbers, but different type and code numbers. The most known types are Echo and Echo Reply. It simply sends a control message to see if someone answers it. It is very useful when verifying network reachability. Echo and Echo reply can be demonstrated with a ping command:
user@computer:~$ ping google.com PING google.com(arn09s05-in-x0e.1e100.net (2a00:1450:400f:804::200e)) 56 data bytes
64 bytes from arn11s11-in-x0e.1e100.net (2a00:1450:400f:804::200e): icmp_seq=1 ttl=55 time=11.4 ms
64 bytes from arn11s11-in-x0e.1e100.net (2a00:1450:400f:804::200e): icmp_seq=2 ttl=55 time=11.4 ms
64 bytes from arn09s05-in-x0e.1e100.net (2a00:1450:400f:804::200e): icmp_seq=3 ttl=55 time=11.9 msTroubleshooting Layer 4 issues
A layer 4 issue could be recognized if the remote service is pingable with ICMP, but the service is still unavailable inside the web browser. That could indicate that a certain TCP or UDP port on the remote end is closed. As long as you have verified layer 3 connectivity with a ping command, the chance for layer 4 issues should be minuscule; unless you are the one hosting the public services.
Most Layer 4 issues are out of your control anyway, and has to be resolved by either the Internet service provider, or the administrator of the application you are trying to reach…
…Not to go too much into detail, (you are free to do it here) but a website could end up only being reachable when IPv6 is turned off on your network. That is because the business hosting the webserver, haven’t made appropriate exceptions for certain ICMPv6 messages in their firewall.
That concludes the Layer 4 Transport Protocol. Next up is the Application Layer.