Installing FreeIPA with DNS service
How-To: FreeIPA
20th July 2023.
Quick start guide: https://www.freeipa.org/page/Quick_Start_Guide
This is a guide on how to install FreeIPA with DNS services.
Preparations
Network Settings
The FreeIPA server is going to have one NIC into the internal service network, where only mgmt and internal users have access to.
What NTP Servers to use
I’m using public NTP servers with IPv6 support. You are free to use the same if you want:
ntp1.bit.nl
2001:7b8:3:2c::123
ntp2.bit.nl
2001:7b8:3:2d::123
Hardware Requirements
You (preferably) need a Redhat or Fedora server installed. Minimum requirements say 2GB of RAM, but these are my settings:
4GB RAM
1vCPU with 2 Threads
1 drive with 40GB storage, Thick provisioning.
1 vNIC adapter
Note: I’m using FreeIPA for home-labbing. Your requirements may be different.
Initial Configurations
These are configuration steps done on the Fedora/Redhat server before installing the FreeIPA software.
Configure hostname
Set a hostname (not FQDN)
# nano /etc/hostname
sauna-ipaConfigure local DNS settings
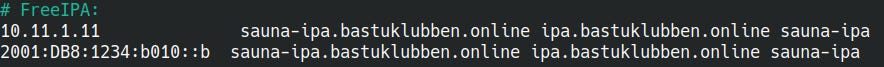
DNS Rules for the /etc/hosts file:
The hostname cannot be localhost or localhost6.
The hostname must be fully-qualified (hostname.ipa.test)
The hostname must be resolvable. (It will be, once you edit /etc/hosts).
The reverse address that it resolves to must match the hostname.
Edit the /etc/hosts file to include the FQDN of the IPA server. The fully-qualified name must come first. Any SAN names can follow. It should look like this:
# nano /etc/hosts
# FreeIPA:
10.11.1.11 sauna-ipa.bastuklubben.online ipa.bastuklubben.online sauna-ipa
2001:DB8:1234:b010::b sauna-ipa.bastuklubben.online ipa.bastuklubben.online sauna-ipaNote: You also need to add these entries above to the remote host you are configuring from, if applicable (if you are using, for example, SSH to the ipa server).
Firewall Openings
Fedora comes with firewalld enabled by default.
sudo firewall-cmd --add-service freeipa-4 --add-service=dns --add-service=ntp --permanent
Verify: It should look similar to this:
# firewall-cmd --list-services
dns freeipa-4 freeipa-ldap freeipa-ldaps kerberos ntp sshNote: For more information about firewalld commands:
https://docs.fedoraproject.org/en-US/quick-docs/firewalld/
Installing the FreeIPA server
From a root terminal:
dnf install freeipa-server
dnf install freeipa-server-dns
Note: If your domain, let’s say bastuklubben.online, is already resolvable by a DNS provider, you will likely get an error. You can either configure a subdomain like "internal.bastuklubben.online” to use for your local services, or you can use the “allow zone overlap” when installing. Be warned though that your public services will not be resolvable from your internal networks; unless you add those entries to FreeIPA.
ipa-server-install --allow-zone-overlap
The log file for this installation can be found in /var/log/ipaserver-install.log
==============================================================================
This program will set up the IPA Server.
Version 4.10.1
This includes:
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the NTP client (chronyd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure SID generation
* Configure the KDC to enable PKINIT
To accept the default shown in brackets, press the Enter key. Do you want to configure integrated DNS (BIND)? [no]: yesDNS Recursion Configuration
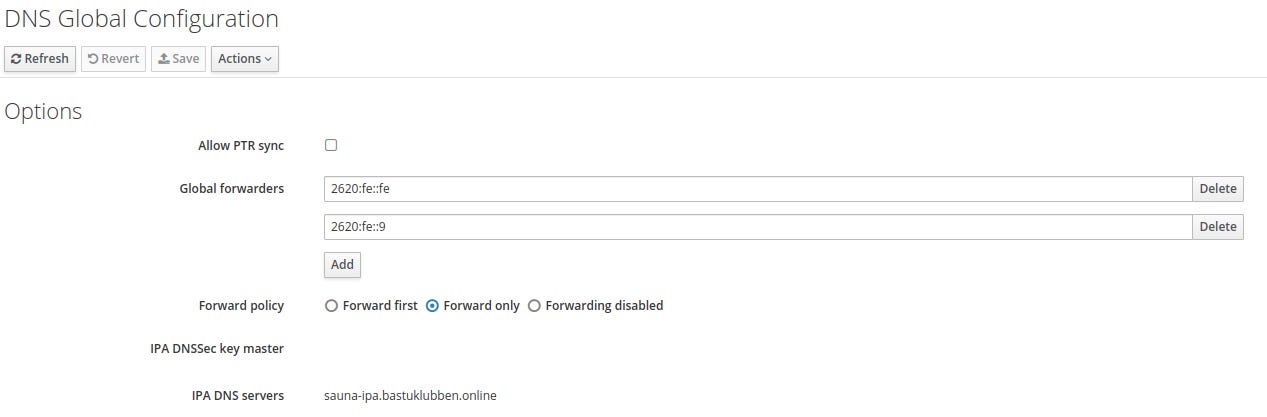
DNS recursion is used to forward DNS requests to a public DNS server, when they are not resolvable by the IPA server.
You should be able to set the DNS forwarders in the installation, but if it fails, here is where you configure it from the WebGUI:
Step 1: In the webGUI: Network Services > DNS global configuration
Set IPv6 addresses
set forward policy to forward only
Note: Apparently, only IPv4 works when using OpenDNS addresses. I switched to use Quad9 and that worked a lot better with IPv6 for some reason.
Step 2: From CLI you have to edit this file to allow recursion for your specific networks:
nano /etc/named/ipa-ext.conf
/* User customization for BIND named
*
* This file is included in /etc/named.conf and is not modified during IPA
* upgrades.
*
* "options" settings must be configured in /etc/named/ipa-options-ext.conf.
*
* Example: ACL for recursion access:
*
*/
acl "trusted_network" {
localhost;
10.8.0.0/13;
2001:DB8:1234:8000::/49;
};Then, enable recursion from this file:
sudo nano /etc/named/ipa-options-ext.conf
/* User customization for BIND named
*
* This file is included in /etc/named.conf and is not modified during IPA
* upgrades.
*
* It must only contain "options" settings. Any other setting must be
* configured in /etc/named/ipa-ext.conf.
*
* Examples:
* allow-recursion { trusted_network; };
* allow-query-cache { trusted_network; };
*/
/* turns on IPv6 for port 53, IPv4 is on by default for all ifaces */
listen-on-v6 { any; };
/* Enable DNS forwarding */
allow-recursion { trusted_network; };
allow-query-cache { trusted_network; };
/* dnssec-enable is obsolete and 'yes' by default */
dnssec-validation yes;Note: The above files are written in C. When you comment in C, you have to put "/*" in the start, and "*/" at the end. If you miss that detail, it can comment out the whole file by mistake.
Step 3: restart FreeIPA:
ipactl restart
Conclusion
That is how you install FreeIPA with DNS service. I hope I didn’t forget any steps. The most frustrating parts for me was the caveat with OpenDNS, and that I had to learn about C commenting the hard way.