FreeIPA: Installing the FreeIPA Client And Some Basic User Configuration
How-To: FreeIPA

24th July 2023
Updated 16th September 2023
Updated 16th August 2025
Updated 1st September 2025
Update: The Installation has become easier for IPv6 users and no longer do you need to manually adjust any settings in /etc to make it work.
The FreeIPA client enables LDAP authentication on your Linux client machines. It automatically configures domain and LDAP settings to work with the configured FreeIPA domain.
The FreeIPA client software can be (in relative terms) easily installed on Linux Distributions that are Debian-based or Redhat-based.
Assumptions
DNS Server is already configured to point to the FreeIPA server. Otherwise you have to manually add the FreeIPA FQDN to the /etc/hosts file.
Create a User
You can do this in the WebGUI, but for demonstration purpose, lets configure it in CLI to speed things up:
Step 1: Establish or renew Kerberos ticket
To be able to administer FreeIPA services, one has to have a valid kerberos ticket. It’s equivalent of logging in to the WebGUI.
On the FreeIPA Server:
kinit admin
[root@sauna-ipa /]# kinit admin
Password for admin@INT.BASTUKLUBBEN.ONLINE:
[root@sauna-ipa /]#To check the validity of the kerberos ticket:
[root@sauna-ipa /]# klist
Ticket cache: KCM:0
Default principal: admin@INT.BASTUKLUBBEN.ONLINE
Valid starting Expires Service principal
07/09/2023 21:49:21 07/10/2023 21:02:07 krbtgt/INT.BASTUKLUBBEN.ONLINE@INT.BASTUKLUBBEN.ONLINEStep 2: Set the default shell to bash (Optional)
Not required but strongly recommended. The default shell for users is /bin/sh. You can change the default shell profile for all users with this command:
ipa config-mod --defaultshell=/bin/bash
Step 3: Create a user
ipa user-add sysadm --first=System --last=Admin --password
[root@sauna-ipa /]# ipa user-add sysadm --first=System --last=Admin --password
Password:
Enter Password again to verify:
-------------------
Added user "sysadm"
-------------------
User login: sysadm
First name: System
Last name: Admin
Full name: System Admin
Display name: System Admin
Initials: SA
Home directory: /home/sysadm
GECOS: System Admin
Login shell: /bin/bash
Principal name: sysadm@BASTUKLUBBEN.ONLINE
Principal alias: sysadm@BASTUKLUBBEN.ONLINE
User password expiration: 20230709195644Z
Email address: sysadm@bastuklubben.online
UID: 1902600005
GID: 1902600005
Password: True
Member of groups: ipausers
Kerberos keys available: TrueInstall FreeIPA Client on Ubuntu/Fedora
The steps below are going to be the same for all distributions unless otherwise specified.
Step 1: Add FQDN to your hostname
sudo nano /etc/hostname
sauna-vm2.int.bastuklubben.online sudo halt --reboot
Update: Also make sure that the hostname is resolvable by the local host:
sudo nano /etc/hosts
2001:db8:1234:a000::2101 sauna-vm1.int.bastuklubben.online sauna-vm1Step 2: Install Free IPA Client:
Ubuntu/Debian:
sudo apt install freeipa-client
Just press enter if this comes up:
Fedora:
sudo dnf install ipa-client
Step 3: Configure FreeIPA Client:
sudo ipa-client-install --mkhomedir
If for some reason automatic domain discovery fails, you can try enter the domain manually:
sudo ipa-client-install --mkhomedir --domain INT.BASTUKLUBBEN.ONLINE --server ipa.int.bastuklubben.online
$ sudo ipa-client-install --mkhomedir
This program will set up IPA client.
Version 4.12.2
Discovery was successful!
Do you want to configure chrony with NTP server or pool address? [no]:no
Client hostname: sauna-vm2.int.bastuklubben.online
Realm: INT.BASTUKLUBBEN.ONLINE
DNS Domain: int.bastuklubben.online
IPA Server: ipa.int.bastuklubben.online
BaseDN: dc=int,dc=bastuklubben,dc=online
Continue to configure the system with these values? [no]: yes
Synchronizing time
No SRV records of NTP servers found and no NTP server or pool address was provided.
Using default chrony configuration.
Attempting to sync time with chronyc.
Time synchronization was successful.
User authorized to enroll computers: admin
Password for admin@INT.BASTUKLUBBEN.ONLINE:
Successfully retrieved CA cert
Subject: CN=Bastuklubben Root CA,O=Bastuklubben,C=NO
Issuer: CN=Bastuklubben Root CA,O=Bastuklubben,C=NO
Valid From: 2025-08-05 18:47:12+00:00
Valid Until: 2055-07-29 18:47:11+00:00
Subject: CN=Bastuklubben Subordinate CA01,O=Bastuklubben,C=NO
Issuer: CN=Bastuklubben Root CA,O=Bastuklubben,C=NO
Valid From: 2025-08-05 19:20:05+00:00
Valid Until: 2040-08-01 19:20:04+00:00
Enrolled in IPA realm INT.BASTUKLUBBEN.ONLINE
Created /etc/ipa/default.conf
Configured /etc/sssd/sssd.conf
Systemwide CA database updated.
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config.d/04-ipa.conf
Configuring int.bastuklubben.online as NIS domain.
Configured /etc/krb5.conf for IPA realm INT.BASTUKLUBBEN.ONLINE
Client configuration complete.
The ipa-client-install command was successful
Step 5: Test
Login with directory user
Either logout and login with a defined user in the FreeIPA domain, or use SSH:
localadmin@testpc:~$ ssh wl@::1
wl@testpc:~$ pwd
/home/wlVerify installation of Root CA
Note: I am running a CA-less setup with external CA server.
Fedora:
less /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pemUbuntu/Debian:
$ ls -l /usr/local/share/ca-certificates/ipa-ca/Note: If you only see the subordinate CA, read this post.
Conclusion
Installation of the FreeIPA Client is becoming very easy now. I was able to remove a few obsolete steps that was necessary in 2023 (unfortunately i had to add another). It’s fascinating how documentation gets outdated so quickly.
Appendix
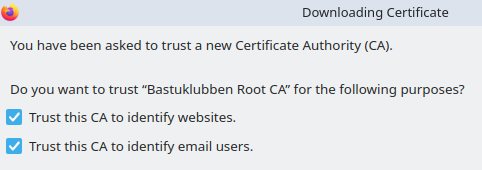
Firefox doesn’t automatically add the Root CA
Firefox has it’s own store and it seems like it’s doesn’t look in the systems truststore for any additional custom CA’s. Therefore you have to add it manually:
Navigate to Settings > Security and Privacy > View Certificates…
Click on the tab Authorities > Import…
Import the certificate stored in /etc/ipa/ca.crt
Trust the certificate for browsing and optionally emails
Legacy configuration
these settings were included in the 2023 version but are not necessary anymore:
Add IPv6 workaround (Only applicable on IPv6 networks):
This bug has been fixed long time ago
sudo nano /etc/sssd/sssd.conf
[domain/bastuklubben.online]
id_provider = ipa
ipa_server = _srv_, sauna-ipa.bastuklubben.online
ipa_domain = bastuklubben.online
ipa_hostname = sauna-nms.bastuklubben.online
auth_provider = ipa
chpass_provider = ipa
access_provider = ipa
cache_credentials = True
ldap_tls_cacert = /etc/ipa/ca.crt
krb5_store_password_if_offline = True
lookup_family_order = ipv6_only
[sssd]
services = nss, pam, ssh, sudo
domains = bastuklubben.online
[nss]
homedir_substring = /home
...sudo service sssd restart
Source: https://pagure.io/freeipa/issue/8243
Edit PAM config to support automatic home directory
This is no longer needed and seems to only make things worse:
nano /usr/share/pam-configs/mkhomedir
Name: Create home directory on login
Default: no
Priority: 900
Session-Type:
Additional Sessions-Interactive-Only: yes
Session:
required pam_mkhomedir.so umask=0077 skel=/etc/skelConfigure automatic creation of home directory (Ubuntu/Debian only)
You can add this but it’s not needed on Debian 12 at least:
sudo pam-auth-update --enable mkhomedir