Foundations of Distributed Ledger Technology Part 1: Problems with centralized infrastructure
DLT Foundations

5th August 2024
Distributed Ledger Technology (DLT) is a new technology that is under rapid development and it has tremendous potential for mankind. The invention of DLT will be remembered as one of humanities greatest achievements, like the invention of the wheel, or the agriculture revolution. It’s so powerful that, if captured and controlled, it can enslave all mankind into a technocratic dystopia. But, if let free and decentralized, can free mankind from all tyrants and tear down borders. Such a powerful technology is worth everyone’s attention, because it will be shaping this century. To explain what it is, we first need to explain what it solves.
The Byzantine Generals Problem
The Byzantine generals problem is an old problem in computer communication and have remained unsolvable until recent times. It goes something like this:
"How do you make absolutely sure that multiple entities, which are separated by distance, are in full agreement before an action is taken?"
Or in other words:
"How can individual parties find a way to guarantee full consensus, without being in the same room?"
Imagine you are a byzantine general that is going to siege a fortress. You have multiple battalions surrounding the city. A successful siege is likely, if all battalions performs an coordinated attack. Defeat will most likely result if the attack is uncoordinated. You have to send out messages to all the generals of the other battalions and receive a reply from each one of them, that confirms that they are ready at dawn. There are many dilemmas with this:
What if the messenger gets killed and no reply is received?
What if the messenger get captured, and a fake reply is returned?
How can the other generals know that the message is actually from you?
What if some of the generals are traitors?
The only way computer communication have been able to work safely is through hierarchical structures with central trusted authorities. Distributed Ledgers like Bitcoin, Ethereum or Hedera claims to have solved this problem, some better than others.
So what is the problem with central communication? I’m going to explain some concrete problems with today’s centralized infrastructure.
Why we need decentralization
We are living in a world that gradually becomes more restricted:
Centralization of Infrastructure - More and more of our data is being stored on a few tech giants infrastructure. What is the problem? Read about what happened to Parler for example. I have written about it in my post about Signal.
Big-Brother style Surveillance - More and more regulations that violates our right to privacy is being drafted and implemented around the world. Thanks to centralized infrastructure, you only have to enforce the rules on a few big organizations.
Reliance on 3rd Parties - We rely heavily on 3rd parties to authorize everything from payments, legal issues and web security. The problem is that those 3rd parties are not immune to corruption.
Censorship - A combination of 1, 2 and 3 has lead to censorship of dissenting opinions. For example googles policies prohibits posting of false claims about voter fraud in previous elections. But who decides what are false claims? Similar policies exists also for medical information. If you disagree with WHO, your opinion is not allowed on Youtube.
Below I will give you two concrete examples of what I believe DLT would do much better.
Public Key Infrastructure and Web Security
Overview of PKI
PKI is the backbone of the security of the Internet today. Without PKI it wouldn’t be possible to have e-commerse, internet banking or anything handling sensitive data. PKI is not one specific protocol, but a suite of protocols that together builds the security of todays Internet. The types of functions include:
Authentication. One of the most important functions of PKI is for a server to prove for the client that it actually is who it claims to be.
Encryption. Protect the communication from unauthorized parties to eavesdrop on sensitive information.
Integrity. To make sure the data hasn’t been altered from one end to another.
Note: I encourage you to view the links in the text below as many of them are videos that are very good at explaining PKI components.
Web Security
You may have noticed that there is a padlock in the address field of your browser whenever you browse a website that has HTTPS enabled, which today is about 99% of the time. It means that the website is secured with TLS = Transport Layer Security, which is one part of the PKI suite.
TLS encryption protects your traffic from 3rd parties to eavesdrop on your traffic. The way TLS encryption is established is through a TLS handshake where the client and the server agrees on what parameters (cipher suite) to choose :
Public Key Signatures, like RSA or ECDSA
Encryption algorithm
Hashing function
If you click on the padlock you can see it says “Connection is secure”. This is because the website has a verified certificate. If you click on details, you see who has verified the certificate.
You may notice that substack.com is verified by Cloudflare Inc. Who is Cloudflare and why should we trust them?
Cloudflare is one of many Internet Service Providers, and one of their services is that they can sign certificates for webpages. The reason why the browser trusts Cloudflare is because their Root CA = Certificate Authority is included in the browsers trusted certificate store.
This is a simplified version of the first two steps in the TLS handshake that is relevant for this post:
Digital Certificates are used by servers to authenticate themselves, i.e. to prove their identity. Digital certificates for webpages works in about the same way as any other type of certificates or licenses. For example, if you have a drivers license, which is issued by one nations transport agency, you are then allowed to drive on roads in many countries, because many countries may trust that this transport agency will only issue driver licenses to people who are competent enough to drive a car. If your transport agency is not on the list of trusted authorities, you may have to take an additional driving test to be able to drive in that country.
Likewise, if you browse a webpage and one of the following occurs:
The webpage doesn’t have a certificate;
The certificate is signed by some authority that is not in the list of trusted authorities;
The certificate is signed by itself, i.e. “I am example.com, trust me”;
or the certificate has expired,
Then the browser will give you a warning screen before you enter the webpage.
So who decides which organizations are trusted to sign certificates on behalf of other organizations? The CA/B Forum (Certificate Authority / Browser), which is a consortium of public certificate authorities and browsers, decides which organizations are trusted to become Public CAs. Therefore the topology looks like this:
When the TLS handshake is established, the connection is authenticated and encrypted communication begins. One important detail about the key exchange and the encryption is that 2 keys are involved: One public key used for encrypting the traffic, and one private key to decrypting the traffic. Only the recipients of the encrypted traffic have access to the private keys.
Now you have an overview of how PKI and Public Key Encryption works, now it’s time to discuss its flaws.
Problems with PKI
PKI works well enough inside an organization where you trust your own servers. On a global scale, PKI has its challenges.
A public CA has a huge responsibility. If hacked or corrupted, it can have devastating effects on the security of the Internet. There have already been many examples of misbehaving CA’s in the past.
PKI Backdoors
Another problem with PKI is that it can be used as backdoors for Big Tech giants and government authorities. On Microsoft windows 11, you can find that Microsoft has included it’s own Certicate authorities, which could be used for sending telemetry data to Microsoft. Even if i don’t know that for sure, there are no restrictions of what Microsoft could do with those certificates.
Qualified Website Authentication Certificates (QWACs)
EU also wants, by legislation, force browsers and OSes to accept their EU Root Certificate, which is going to be used to give everyone a digital identity, so they will know what everyone is doing on the Internet.
People are talking about how web encryption will be broken by Quantum computers, but they are not needed when you have a backdoor through a “trusted” root CA.
A story about PKI Abuse
Symantec, the company behind the famous Norton Antivirus, acquired Verisign in 2010. Verisign was one of the largest Public CA’s in the world, worth at least a billion dollars. How much of the market they owned is hard to find the answer to. I have heard 80% but I haven’t been able to verify that.
In 2016 Symantec also acquired Blue Coat Systems, which tools have been used by repressive governments to control and monitor the population. Antivirus software is in itself invasive on ones computer, so you can say it’s a match made in heaven… or in hell in this case.
To make things more interesting, Blue Coats CEO became CEO for Symantec. So we had this company being both a trusted public CA, while at the same time dealing with surveillance systems for repressive governments. Absolutely no conflict of interest there…
In 2017 someone at Google checked the certificate issuer for google.com and noticed that the certificate was issued by Blue Coat, which was not authorized to issue certificates for Google. Having issued trusted certificates for google.com, Symantec could then decrypt traffic going to google before sending it to google.com, becoming a MITM = Man In the Middle.
Google decided to remove Symantec as a trusted public authority on their chrome browser. After some legal battles, in 2019 Symantec had to give in and the company basically imploded. The Verisign part got sold to Digicert for a lower sum than what they had acquired it for. And Symantec is now a part of Broadcom.
This is not the only time Google have had their digital certificate faked. At least two other similar exploits has happened since; one that affected Google users in Iran and the other affected Google users in China.
A hack or a feature?
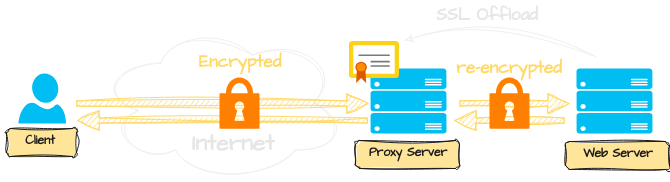
What all these companies did to Google and others is a type of a MITM= Man-in-the-Middle attack, but it is similar to the concept of SSL Offloading.
SSL Offloading is where a frontend proxy server has the certificate and receives the traffic from clients. It then decrypts and re-encrypts the traffic and forwards it to the “real” server.
Note: SSL = Secure Socket Layer was invented by Netscape and became the defacto standard we know today as TLS. Both acronyms are still used interchangeably.
I have written about how to setup SSL-Offloading before. If you would reach some of my public services, you wouldn’t know the difference if you were talking to my firewall, or the backend server itself. This is a good feature because it hides my internal IP addresses and protects my servers. But at the same time, this technique could be used for malicious purposes. How do you know for sure that when you are using Googles services, that they are not performing SSL offloading to send the traffic via NSA or some data collector?
The Moral of the Story
This shows how “trusted authorities” cannot be trusted. I don’t know what incentive Symantec had to start issuing fake certificates, but one theory is that they maybe had a lucrative deal with some three-letter agency. When you consider Blue Coat and their regular customers, I don’t think the leaders of Symantec had much of a moral standard.
Even if I can’t prove that’s the case, the fact that it can happen, most probably means that it will happen. The Internet traffic might be relatively safe from hackers, but is not safe from corrupt authorities and regulations.
Central banking
Most people don’t have a clue on how the banking system works. If that is you, I suggest you start with watching through Mike Maloneys Hidden Secrets of Money, especially part 4.
After you have educated yourself, you now know that today’s currencies are fiat currencies that are only backed by the faith on the government, which is in free-fall all over the world. There are many problems with this but I will only address the two biggest ones, in my opinion.
Note: I suggest you read The Creature From Jekyll Island if you want a comprehensive list of all the problems with today’s economic system.
Printing Money without Backing
Since fiat money can just be printed into existence by the powers that be, the currencies will eventually become worthless. By printing the value into oblivion, the governments and bankers basically steals your purchasing power through inflation. You might have noticed a rapid raise in prices the last few years. At the same time, there has been a huge increase in money supply:
Note: We can see that the supply of money has decreased a bit the last year or so. I’m no expert but I believe that is because people are generally spending less and trying to pay of high interest loans. When currency meets debt they annihilates each other, as all fiat currency is based on debt.
After President Nixon abolished the gold standard in 1971, the dollar has lost about 90% of it’s purchasing power.
When you realize this, do you think it makes sense to save fiat currency in a bank account? This trend puts the dollar as the world-leading currency into question.
Note: What if you don’t live in the United States? All major currencies in the world is tied to the dollar, thanks to the bretton-woods agreement. Some countries are now trying leave the dollar system and go back to a gold standard, I’m talking of course about the BRICS alliance. However, many countries in the western world will still be affected by a crashing dollar.
Central Control
You may not know about this problem until it happens to you, but there are certain things you are not allowed to purchase. I’m not talking about drugs or firearms by the way.
I have noticed that the banks are becoming very interested in what you do with your money lately. A personal anecdote is when I sometimes try to buy larger amounts of crypto currencies; it gets blocked and I have to negotiate with them and fill in forms to prevent money laundering they claim, for them to approve of the transaction. Some crypto brokers am I not even allowed to buy from, like Moonpay. The bank claims that they have had many reports of scams from there, but I personally never had any issue with them before they were blacklisted. I have heard about other people experience similar problems too, even when they have bought gold and silver.
Dissenting opinions get their bank accounts frozen
Even worse is it for people that is trying to break the narrative. There are many, likely thousands of examples of people all over the world that had their bank account frozen for their political views. Here is one example of where Nigel Farage, Leader of the Reform UK party, speaks about his experience when his account got frozen:
Freedom Convoy
Another alarming banking scandal was when the canadian truckers got their bank account closed for demonstrating against vaccine mandates.
The governments narrative is that it was justified because the blockades were illegal and needed to be stopped… but it is a crime against humanity to not allow people the right to decide over their own body, and remove their means of providing for themselves! The truckers and their supporters were only fighting for their rights. When protests fall on death ears, what do you do? This demonstrates the powers the establishment have over us.
It’s very alarming already, but with CBDC = Central Bank Digital Currency, we will be totally screwed.
Wikileaks
Since 2010, Wikileaks have been banned from Paypal, VISA and Mastercard et al. There was never any lawful grounds to put them on the financial blockade list.
Wikileaks wouldn’t have been around today if it wasn’t for bitcoin. Cryptocurrencies like bitcoin makes it possible to transact between people without needing a bank as an intermediate. For a long time I didn’t get the hype with bitcoin. When I realized this, I now understand why this technology is so powerful and why the establishment is so afraid of it.

Note: More on DeFi = Decentralized Finance, in part 4.
Distributed Ledgers
A distributed ledger is a group of computers that want to come to an agreement on something. For example, when a transaction from Alice to Bob was executed. The protocols are designed to be trustless, meaning you should not need to rely on any authority. The facts on the ledger should be self-evident for anyone to see. Distributed Ledgers have all some degree of BFT = Byzantine Fault Tolerance. There are many variants of it, depending on the specific ledger.
So how does a decentralized ledger look like? First, think of what a traditional ledger is; A book containing records of interesting data. (Can also be synonymous to a database). Examples of ledgers (obviously before the computer age) are:
Accounting books recording orders received from customers, how much they are going to pay and if they have paid or not;
It could also be a guestbook at the hotel, with records of which rooms the guests are staying in, and for how long they are staying there.
Those kind of ledgers are centralized at one location, specific for one organizational entity. A distributed ledger, is therefore a ledger that is available for anybody to view and add entries into, and there can be multiple copies of it.
But how can complete strangers come to an agreement on what entries are valid, and in what order they should be entered in? That is what a consensus algorithm is used for, and that is covered in part 2.
Appendix
Special Mention
Explaining PKI for laymen is not an easy thing to do. I want to thank Computerphile for their videos explaining public key cryptography.
I also want to thank Rob Braxman for all his examples on when PKI can be, or have been used maliciously.